Group Policy to Intune Migration
This is a big one, folks. It’s been a long time coming and my whole team is legitimately thrilled to have this now.
In case you’re not as hyped as me yet, here’s some backstory. For Windows devices managed with Intune and joined to Azure Active Directory, there is no way to implement existing group policy on the machine. Obviously, this would need to be addressed if there was any hope for PCs to be managed in the cloud. Microsoft’s first stab at this was the MDM Migration Analysis Tool, or MMAT, for short. This tool would run on an existing domain join machine and spit out an excel report of which policies were available in Intune as CSP profiles (modern Intune settings).
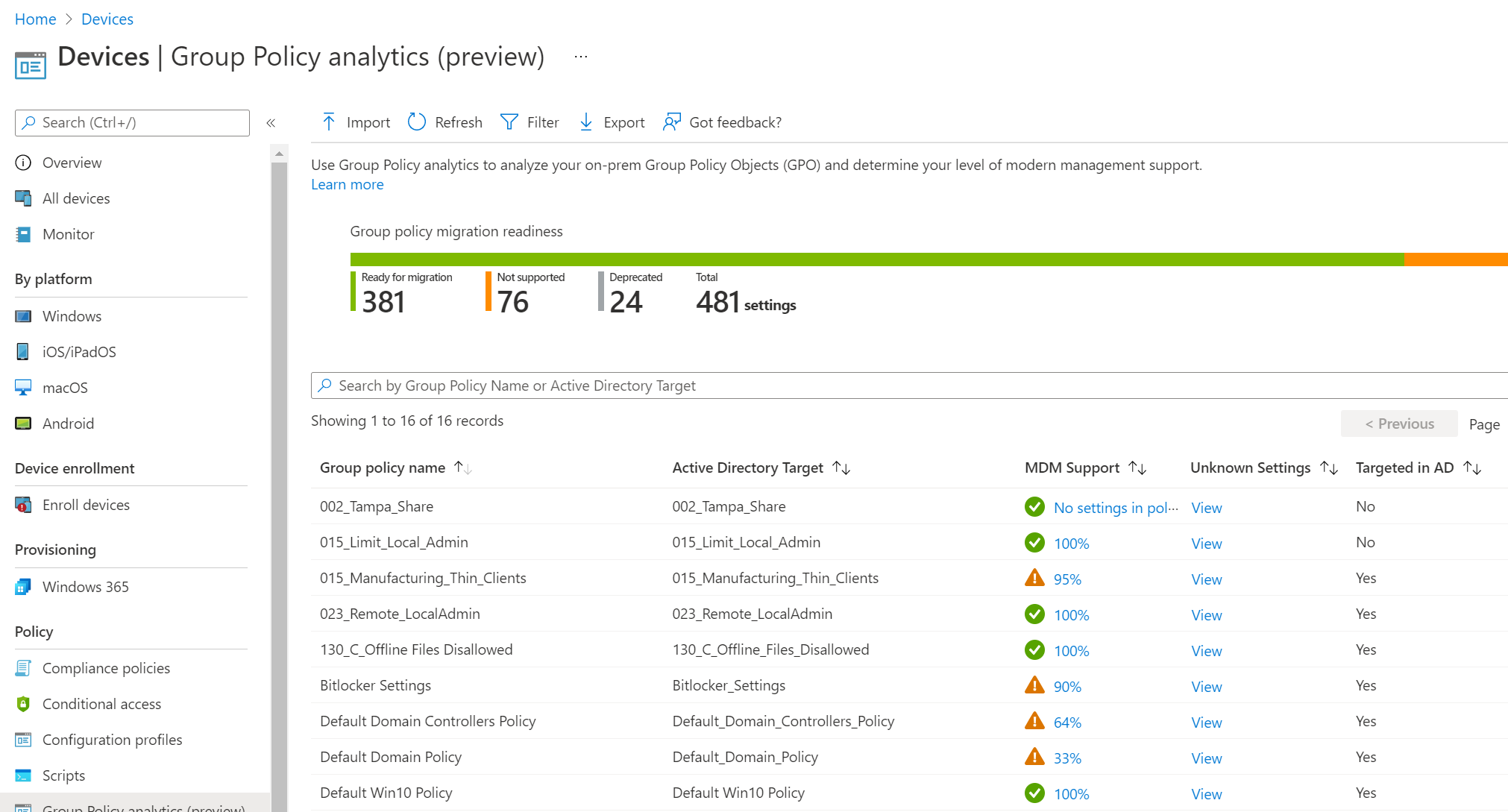
After realizing how tedious it was, Microsoft then implemented Group Policy Analytics in Endpoint Manager. This time, you could export your GPO right from the domain in an XML file and upload this to Intune. You were then presented with an amazing chart that broke down how many of your policies are compatible with Intune and what the path is to set them. While fancy looking, there was just one issue; you could only look.
If you decided that you wanted to migrate 100 of those compatible settings, you would have to go line by line and configure them yourself with either the settings catalog, administrator templates or a custom policy. Depending on how many are required, you’re easily looking at hours, if not days of manual work.
The solution
So how exactly are we going to automate this process? Here’s the flow:
Use GPO Analytics as you would today to have Intune sort through them. Follow the instructions in the link above.
Export the GPO Analytics results from Intune to a csv file.
Run the PowerShell script (which leverages the Microsoft Graph API) we’re about to discuss.
Enjoy!
That’s it! Seems simple enough right? Let’s go into the steps including the permissions needed for the script and how to run it.
Ask for permission
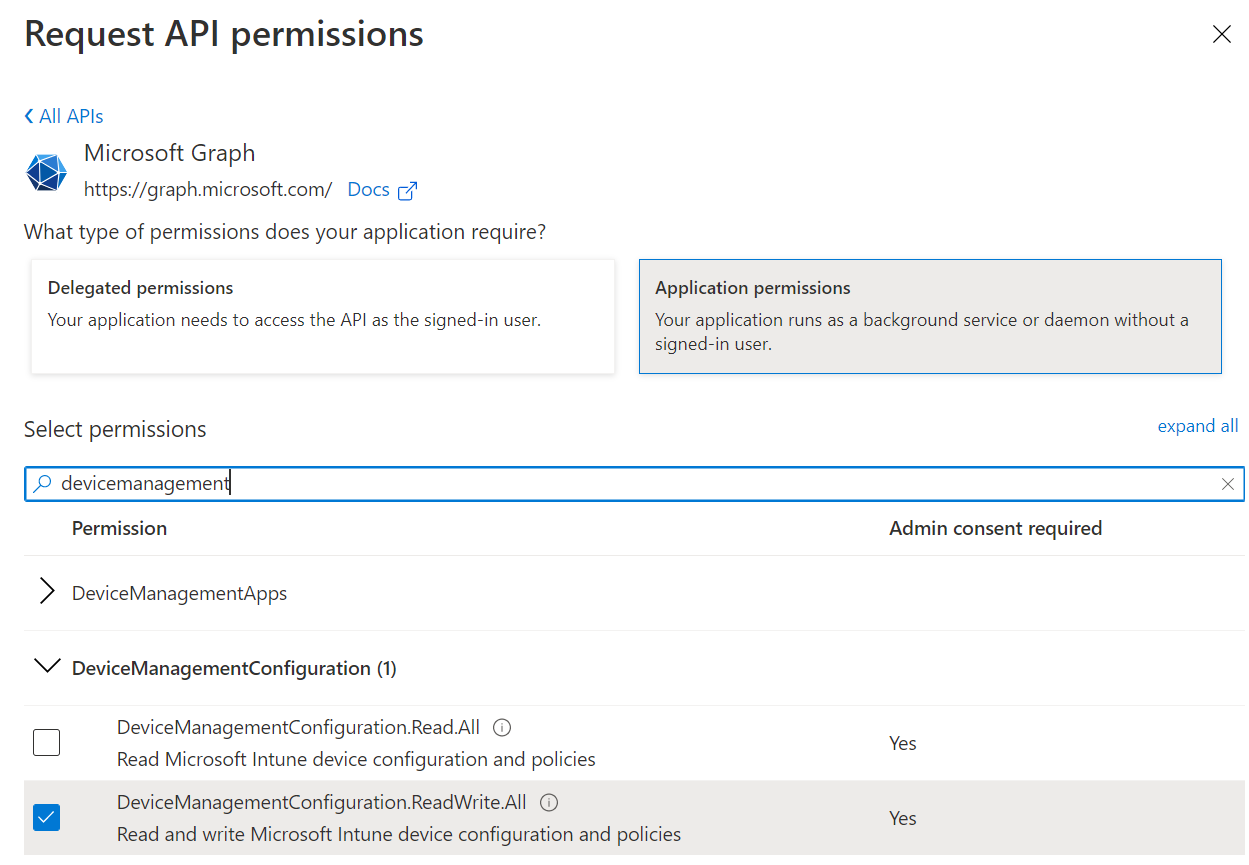
As with most PowerShell scripts that leverage the Microsoft Graph API, we need the script to authenticate with the appropriate permissions in order for it to do, well, what it needs to do. Create an Azure app registration and make note of the Client ID and Secret values. If you haven’t done so, please read Mr. Michael Niehaus’s blog on how to do so here.
Make sure to provide the app registration Microsoft Graph -> Application permissions -> DeviceManagementConfiguration.ReadWrite.All permission and grant consent.
Two important files
Once you’ve ran Group Policy Analytics, go ahead and export the results. You should get a .csv file with all the policy in it. Because of the formatting, you’ll need to switch the headers in the Intune downloaded version to the one in the template I created. You can download it here: template.csv.
Replace the first row with the one in my template. Then go ahead and filter out any unsupported or duplicate policy. It’s time to download the second, and most important file, the actual PowerShell script: gpoToCspMigration.ps1.
Minor edits
For the script to work, you have to add your own personal touch to three areas.
First, replace lines 33, 34 and 35 with your own values from the app registration you created earlier:
Next, set the full path to your .csv file on line 54:
Lastly, choose your own name for the policy on line 195:
With those edits complete, go ahead and run the script. If all goes well, you should end up with your new policy in Endpoint Manager in Device -> Configuration Profiles.
Just because we can, should we?
I’ve always preached about modern management and how organizations need to abandon technical debt. This is still my preference and if you can deploy PCs through Intune with security baselines and configuration profiles, then more power to you.
The reason I decided to create this was two fold. First off, there are some situations where the policy is required and manually combing through the corresponding CSPs is just way too time consuming.
Secondly, I often find folks who aren’t sure if they need to keep certain policies or not. In that case, what better way to test then deploy the settings straight from GPO analytics in addition to security baselines and modern policy. Intune will report on conflicts, you can be sure of that. If the policy we applied does indeed conflict, then we know it is no longer needed.
Whichever reason you end up needing to migrate policies over, at least we can finally do more than just look!